In
this blog I will discuss the obfuscation and payload of an autoit Trojan spy
malware that seems to have different detection name with different AV company.
Sha1:
c06770b5a568404b3167d287f4fa6f0d4305a936
Sha256:
9307773457add5c033fc2505c947b091f213c833b9c41d302d083452fb08a0f2
 |
| different detection name |
Black box
analysis of the file:
Drop
copy of itself in its created folder %appdata%\Roaming\Windata.
%AppData%\Roaming\Windata\MDZYTH.exe
Drop
a component file:
%AppData%\Local\Temp\HTNYEL.vbs
Add
several registry entries as part of its installation process.
HKEY_CURRENT_USER\Software\Win32
HKEY_CURRENT_USER\Software\Win32 HTNYEL "2680"
Add
REGRUN entry to persist on the infected machine.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run HTNYEL ""
%AppData%\Roaming\Windata\MDZYTH.exe""
But due to some checking or some other component it needs you cannot see the other payload done by this malware so we will go now to the interesting stuff. reverse engineering!!! :)
Static Analysis:
Upon extracting the autoit script to the compiled autoit executable you can see that the file was obfuscated and encrypted.
 |
| some obfuscated and encrypted part of au3 script |
Decryption Routine:
by analyzing the
script, I found out that it use a decryption function that contains 2
arguments (in this case it was the "E6ZS0RR7R"). The first argument is
the actual encrypted script and the 2nd argument is the decryption key
(in this case it was the "$H3LW6XV9CR7S" ).
The decryption routine is quite simple but effective to hide the actual string value.
 |
| decryption key |
 |
| decryption routine |
since stable autoit debugger is not quite available in the wild (as far as I know :)). I simulate the decryption routine in Python script, decrypt the string and save it to another file.
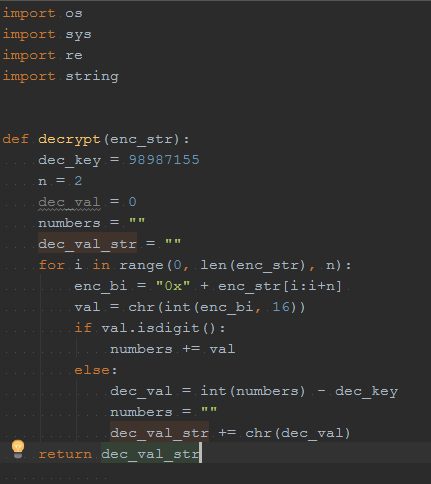 |
| decryption routine in python |
after decrypting the string it was quite readable now and much easier to understand even the variable name is obfuscated.This technique makes the static analysis more difficult.
 |
| after the decryption |
Some of its Payload:
Now we will discuss the behaviors and payloads of this malware that cannot be seen right away in normal black-box testing.
Notable string and filename that may it need to complete the infection to the targeted machine.
 |
| components and notable string |
Monitor some AV product and send this information to its C&C server.
modify the host file of the infected machine.
 |
| modify the host file |
add image file execution registry.
 |
| image file execution |
if the use is the admin , gather the active port , the .exe that are responsible for the active ports and also its process ID.
 |
| netstat command for parsing active ports |
check the type of the drives that are connected to the infected amchine and send it through C&C server.
 | |
| parsing drivetype |
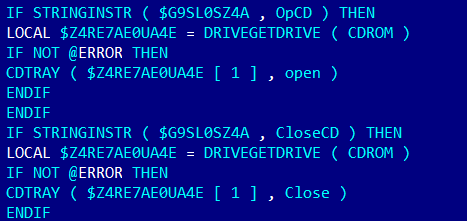 |
| playing around with cdrom tray |
run its keylogger.
 |
| keylogger component |
 |
| part of decoded keylog scripy |
 |
| another .exe and script |
 |
| decoded script that parse the running process |
In this sample we can say how powerful the autoit compiler to control the system. :)
enjoy!!!



