In past few days, I decided to analyze the infection chain of the RIG exploit kit that deliver GandCrab Ransomware in the wild, in credits of malware traffic website.
In this part, I will do a brief analysis of the network packets.(thanks to malware-traffic-analysis for a clean pcap). so lets do the analysis for fun! :)
The first interesting stuff is the HTTP GET with long URL link. This is the landing page of the Exploit kit. We can see by using Wireshark the user agent, size and etc used by this HTTP '
 |
| the first GET command |
 |
| the obfuscated landing page of 2 URL served by the exploit kit. |
after the infected machine engaged to the exploit kit landing page, The exploit kit server response with exploited SWF file and its malware payload which is a GandCrab ransomware in this case.
 |
| the SWF exploit response of EK server after engaging with landing page |
 |
| The compressed SWF file request info |
Then on frame 47 that ends in frame 157 another HTTP GET request coming from the infected machine to the exploit kit server which is the payload of the attack. The EK server response with an encrypted blob of data that will be decrypted as ransomware.
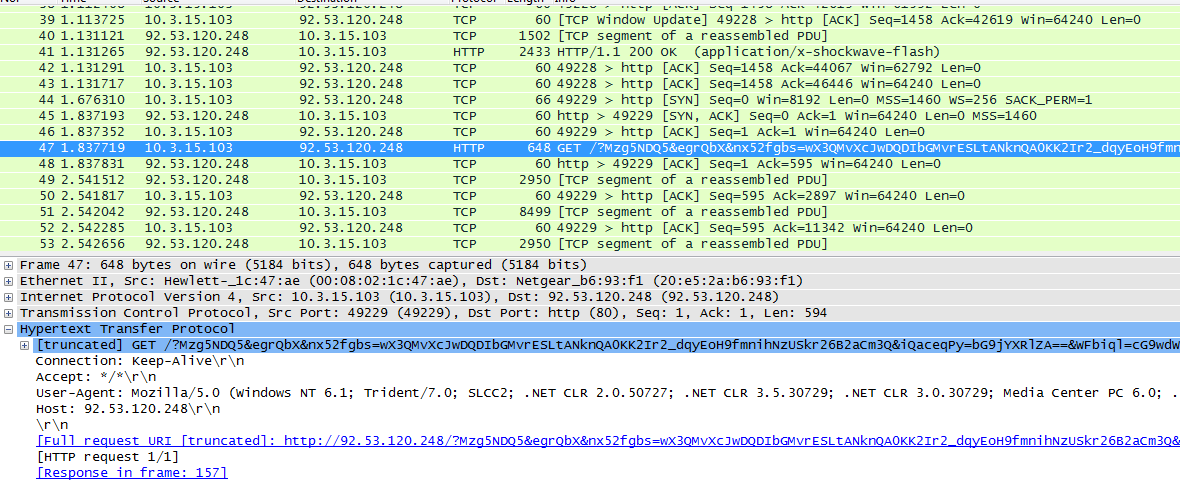 |
| The encrypted payload of delivered by the exploit kit. |
 |
| tcp stream of the payload traffic |
Now we have some idea how infections happen, we will go now in analyzing the main part of the landing page of the exploit Kit. and how the landing page decrypt the blob it downloads to the infected machine.
link to part II.


