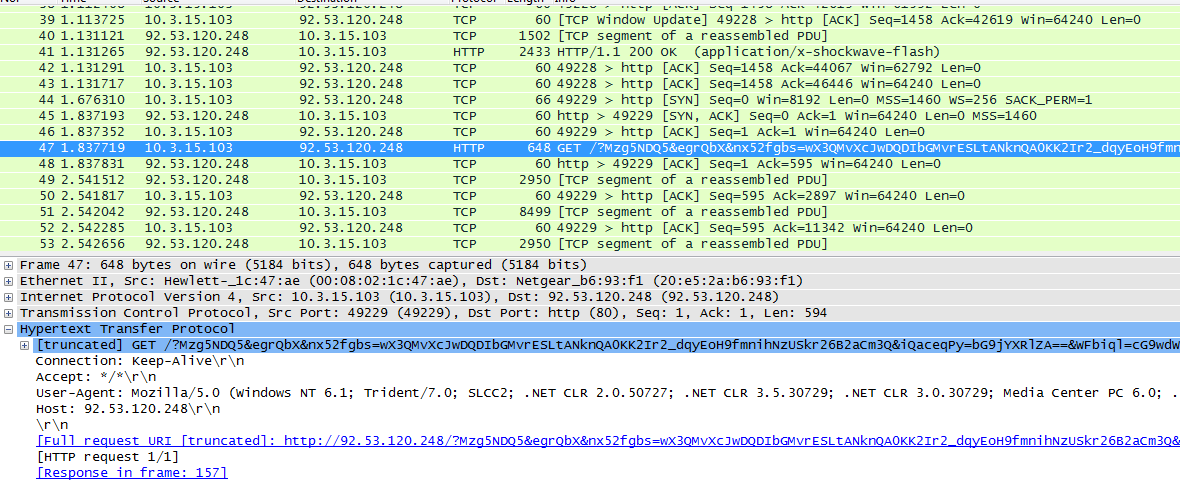
Now we will go through to the payload and the SWF file. :)
The Exploitable SWF File:
for me, one of the trickiest file to analyze is the SWF, because debugger for this file type are not so often seen in public, So usually the way to analyze this as far as I know is through black-box, code decompiler and static analysis of the code.
The SWF file downloaded by this EK are compressed SWF, but nicely the jpex decompiler manage to decompile it.
some noteworthy code in the SWF show that this was related to CVE- 2015-8651.
 |
CustomByteArray
objects are sprayed on the heap first |
The Payload Gandcrab Ransomware:
The ransomware payload was packed to hide the actual code from static analysis. After unpacking the file you can see some noteworthy behavior through static analysis. I mentioned some of it below.
It tries to terminate specific process name related to Microsoft office, database application, and Anti-virus application component to avoid some open handle error during encryption process.
 |
| terminated process |
It tries to check if the keyboard layout is Russian keyboard layout = 419, if yes exit the process.
 |
| keyboard layout checking |
it will also gather other information that will be send to its C2C server that are shown below.
 |
| parsing the Productname of Infected machine |
 |
| parse Processor description |
 |
| check if disk are with following types. |
 |
| how much diskspace are available |
 |
| if the infected machine has the following Anti-Virus installed |
 |
| and other stuff it tries to parse and send to C&C server. |
this ransomware generate RSA encryption key using Crypt API.
 |
| Generate RSA Encryption key |
the Encryption process and the drop .txt file for this ransomware.
 |
| encryption routine |