https://app.any.run/tasks/8a404eaa-f7f5-425a-a49f-ae9138ce8e1c/
Covid-19 Loader:
The note worthy behavior of this loader is extracting all of its main component to the infected machine by parsing its .rsrc section with rsrc entry type 0x0A (RAW_DATA).| figure 1: parsing the .rsrc entry |
It also fetch the langauge identifier to get the language name of the infected machine and check if it is "deutsch". if yes it will use the deutsch version of its message to the user otherwise it will use english.
| figure 2: check machine language |
COVID-19 FOLDER:
It will create a folder name as "COVID-19" in homedrive with hidden attribute that contains all the component of this malware. The wallpaper and the cursor.cur will be used as soon as the machine was already infected and you will notice this before it request to restart the machine.| figure 3 : the components of this malware |
I . mainWindow.exe - The GUI Announcer:
This file is responsible of creating the window UI that will be shown during the infection.This UI will tell the user that the computer was already infected and some windows tools will not working.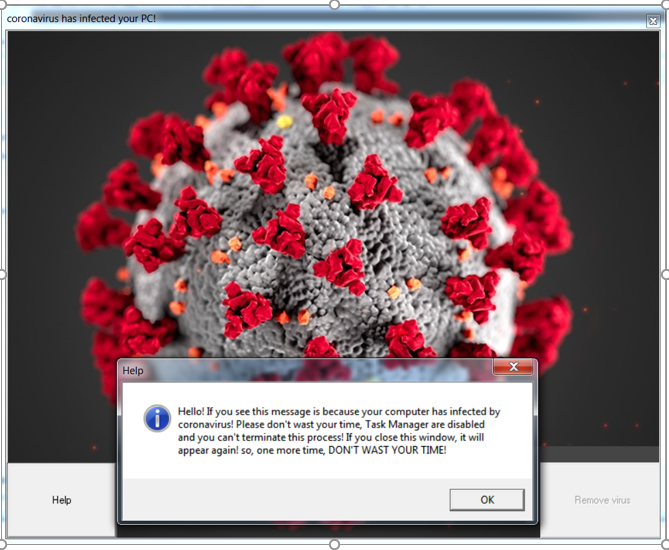 |
| figure 4: UI of this malware including its help message |
II. run.exe - Execution and Persistence:
This is the component file that is almost a copy of the actual loader, where it also contains the language checking and batch files in the .rsrc section with additional entry where it will execute the mainwindow.exe. |
| figure 5: the batch file in run.exe |
III. end.exe - The MBR Killer :
This is the executable that are responsible in modifying the MBR. First it will allocate and initialized SID memory and check the Token membership of that SID. |
| figure 6: check the token membership of the SID |
Then it will read the \\\\.\\PhysicalDrive0 where the MBR reside. the 0x200 bytes original MBR will be converted into hexAscii that will be compared to the hexAscii value of the bad MBR reside on its code. The modification of MBR start with writing the original MBR to the boot sector, next it will write the malicious MBR in same sector and last it will write its message in same sector that will be printed out upon reboot.
 |
| figure 7 : the malicious MBR |
 |
| figure 8: the original MBR |
 |
| figure 9: the code that do the MBR modification |
 |
| figure 10: MBR message |
The malicious boot sector will only try to display the message in write in the boot sector memory. where it prints the each character using si register as the index ptr and int 10.
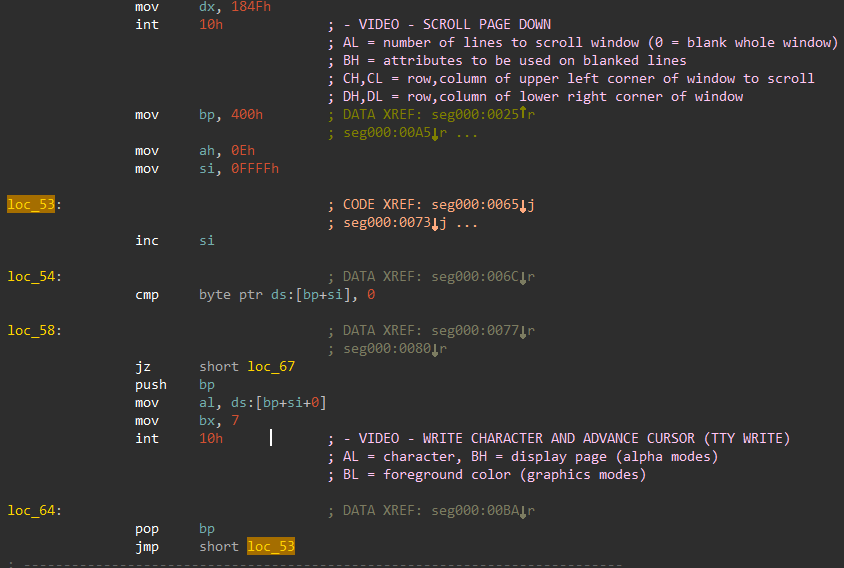 |
| figure 11: the malicious boot sector |
IOC:
sha1: b87405ff26a1ab2a03f3803518f306cf906ab47fmd5: 9dbbfa81fe433b24b3f3b7809be2cc7f
sha256: dfbcce38214fdde0b8c80771cfdec499fc086735c8e7e25293e7292fc7993b4c
filename: KillMBR1
sha1: b2f4288577bf8f8f06a487b17163d74ebe46ab43
md5: 7def1c942eea4c2024164cd5b7970ec8
sha256: c3f11936fe43d62982160a876cc000f906cb34bb589f4e76e54d0a5589b2fdb9
filename: end.exe
sha1: d29cbc92744db7dc5bb8b7a8de6e3fa2c75b9dcd
md5: e6ccc960ae38768664e8cf40c74a9902
sha256: b780e24e14885c6ab836aae84747aa0d975017f5fc5b7f031d51c7469793eabe
filename: mainWindow.exe
sha1: 44fac7dd4b9b1ccc61af4859c8104dd507e82e2d
md5: b1349ca048b6b09f2b8224367fda4950
sha256: c46c3d2bea1e42b628d6988063d247918f3f8b69b5a1c376028a2a0cadd53986
filename: run.exe
YARA:
import "pe"
rule covid_mbr_gui {
meta:
author = "tcontre"
description = "detecting covid_19_main_window"
date = "2020-04-08"
sha256 = "b780e24e14885c6ab836aae84747aa0d975017f5fc5b7f031d51c7469793eabe"
strings:
$mz = { 4d 5a }
$s1 = "coronavirus has infected your PC!" fullword
$s2 = "Task Manager are disabled" fullword wide
condition:
($mz at 0) and all of ($s*)
}
import "pe"
rule covid_mbr_killer {
meta:
author = "tcontre"
description = "detecting covid_19_end_exe"
date = "2020-04-08"
sha256 = "c3f11936fe43d62982160a876cc000f906cb34bb589f4e76e54d0a5589b2fdb9"
strings:
$mz = { 4d 5a }
$c1 = {8A 03 C1 E8 04 40 BA DC 83 40 00 8A 44 02 FF 5A 88 02 8B C5 }
$c2 = {8B D6 03 D2 42 03 C2 50 8A 03 24 0F 25 FF 00 00 00 40 BA DC 83 40 00 8A 44 02 FF 5A 88 02}
$d1 = {6A 00 68 F4 B7 40 00 68 00 02 00 00 68 FC C5 40 00 53 E8 ?? ?? ?? ?? 6A 00 6A 00 68 00 02 00 00}
$d2 = {53 E8 ?? ?? ?? ?? 6A 00 68 F8 B7 40 00 A1 F4 B7 40 00 50 68 FC C5 40 00 53 E8 ?? ?? ?? ?? 53 E8}
$s1 = "WobbyChip" fullword
condition:
($mz at 0) and $s1 and 1 of ($c*) and 1 of ($d*)
}
import "pe"
rule covid_runner {
meta:
author = "tcontre"
description = "detecting covid_19_unpack_run_exe"
date = "2020-04-08"
sha256 = "c46c3d2bea1e42b628d6988063d247918f3f8b69b5a1c376028a2a0cadd53986"
strings:
$mz = { 4d 5a }
$c = {68 0A 00 00 00 FF 74 24 04 FF 74 24 14 E8 ?? ?? ?? ?? 89 44 24 04 83 7C 24 04 00 74 24 FF 74 24 04 FF 74 24 10 E8}
$s1 = "%homedrive%\\COVID-19" fullword
$s2 = "disabletaskmgr" fullword
$s3 = "NoChangingWallPaper" fullword
$s4 = "ADD HKLM\\software\\Microsoft\\Windows\\CurrentVersion\\Run" fullword
condition:
($mz at 0) and 2 of ($s*) and $c
}


